IS Security & Monitoring
HA Firewall Cluster & Wazuh SIEM
Design of a partitioned architecture (6 zones), secured by a redundant firewall cluster (PfSense/OPNsense) and proactively monitored (Splunk, Wazuh, SNMP).
🛡️ Defense Strategy (Risk Analysis)
Risk analysis led to a Zero Trust architecture. Every flow is inspected, and critical assets are isolated by watertight security zones.
Technologies
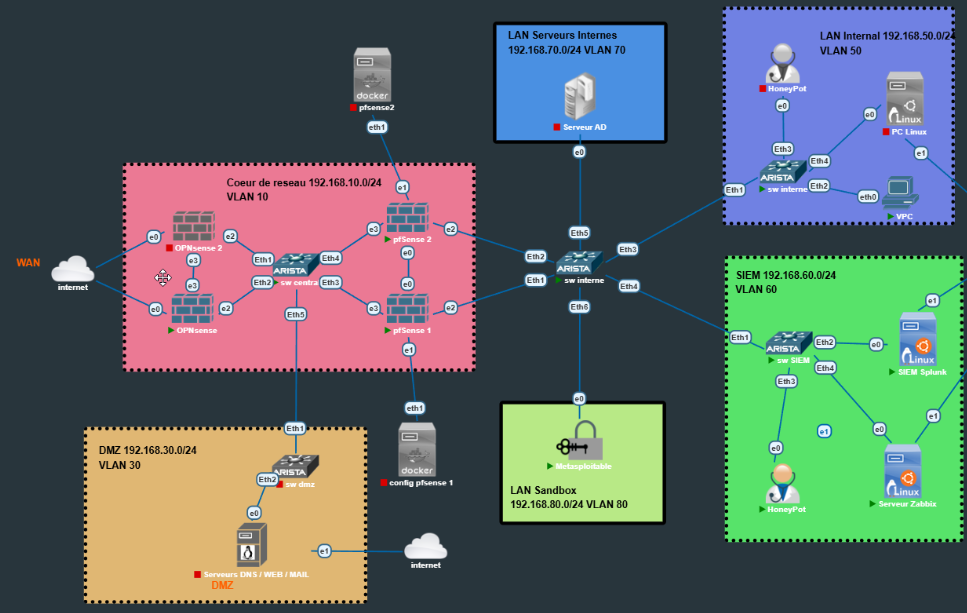
High Security Architecture (6 Zones)
VLAN SegmentationTopology centered around a filtering network core, isolating public services (DMZ) from sensitive data (LAN) and management (SIEM).
🔥 Firewall Cluster Configuration
Implementation of High Availability (HA) between PfSense and OPNsense to ensure service continuity.
Configuration of LAN, WAN interfaces, and a dedicated SYNC interface (10.0.0.x) for replication traffic.
Creation of Virtual IPs (VIP) for the gateway. Automatic Master/Backup failover without connectivity loss.
Real-time synchronization of configuration (rules, aliases) and state tables (TCP sessions) between nodes.
Forcing outbound IP on the WAN VIP to ensure cluster transparency towards the Internet.
Active Monitoring
Multi-level approach for total visibility.
💥 Attack Scenarios & Detection
Validation of robustness via intrusion tests (Red Teaming) from the "Sandbox".
- 🔴 Reconnaissance: Nmap scan detected by firewall IDS rules and escalated to Wazuh.
- 🔴 DDoS (Syn Flood): Saturation attempt absorbed by the cluster and alerted via Splunk.
- 🔴 Intrusion: Attack on the Honeypot blocked and traced for analysis.